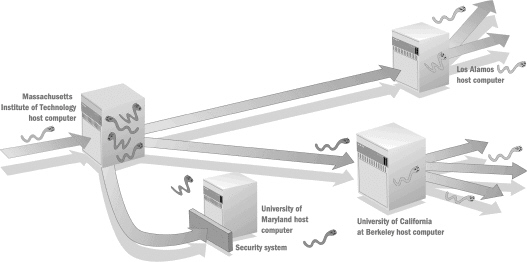
 In the figure above, the worm enters the original host and other unprotected hosts using ____.
In the figure above, the worm enters the original host and other unprotected hosts using ____.
A) infected files
B) a backdoor
C) e-mail
D) a packet
Correct Answer:
Verified
Q55: Which of the following is NOT an
Q56: Q57: A _ contains your computer's settings. Q58: Which of the following is NOT an Q59: A facility that is designed to house Q61: _ protocol refers to any method that Q62: Human error, also called _ error, includes Q63: A(n)_ attack helps hackers guess your password Q64: Malware is created and unleashed by _. Q65: _ authentication verifies identity using two independent![]()
A)restore point
B)recovery
A)black
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents