Consider the following image of a packet capture: 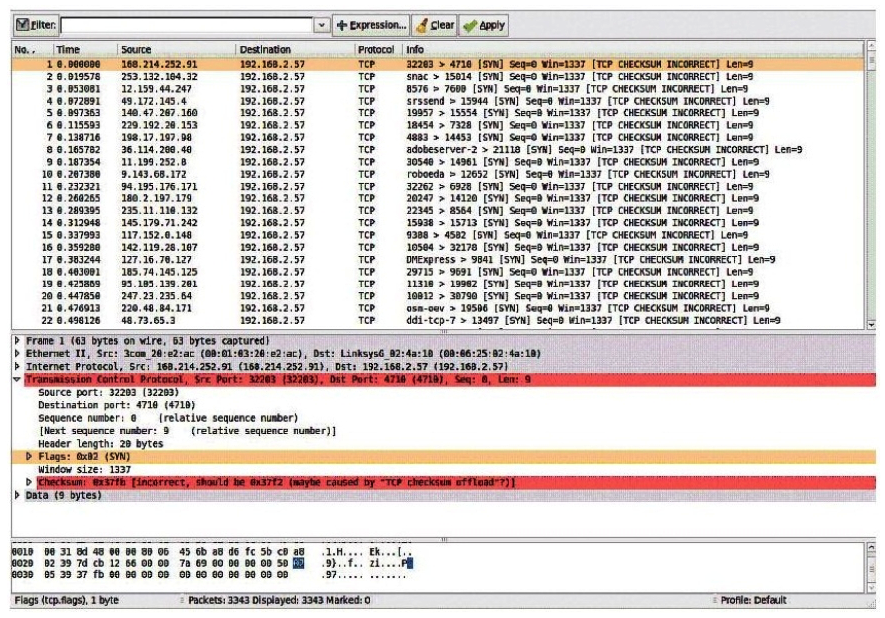 This packet capture has recorded two types of attacks. Which choice lists both attack types?
This packet capture has recorded two types of attacks. Which choice lists both attack types?
A) A dictionary attack and a worm-based attackA.A dictionary attack and a worm-based attack
B) A syn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C) A worm attack and a botnet attack C.A worm attack and a botnet attack
D) A SQL injection attack and a virus attackD.A SQL injection attack and a virus attack
Correct Answer:
Verified
Q34: You have determined that an attack is
Q35: Which of the following activities is the
Q36: You have just deployed an application that
Q37: Which of the following is a primary
Q38: Which algorithm can use a 128-bit key,
Q40: Consider the following image: Q41: Which of the following is a primary Q42: At what layer of the OSI/RM does Q43: What is the primary strength of symmetric-key Q44: Consider the following diagram: ![]()
![]()
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents