Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd. 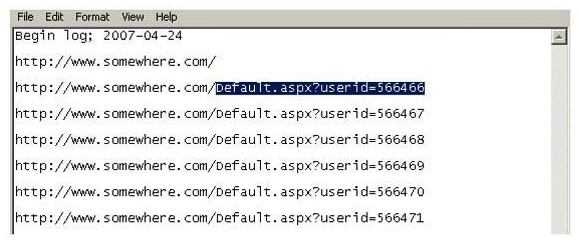 From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
A) Parameter tampering
B) Cross site scripting
C) SQL injection
D) Cookie Poisoning
Correct Answer:
Verified
Q36: When marking evidence that has been collected
Q37: The following is a log file screenshot
Q38: In handling computer-related incidents, which IT role
Q39: What will the following command accomplish in
Q40: All Blackberry email is eventually sent and
Q42: What will the following Linux command accomplish?
Q43: Harold is finishing up a report on
Q44: Paraben Lockdown device uses which operating system
Q45: Why would you need to find out
Q46: What must be obtained before an investigation
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents