Click the Exhibit button. 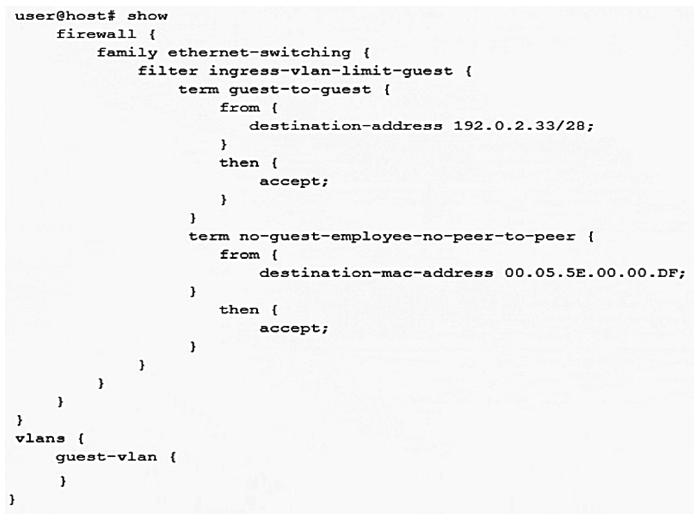 A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic. In this scenario, what must you do to implement the security policy?
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic. In this scenario, what must you do to implement the security policy?
A) Implement 802.1X on the guest VLAN
B) Attach the filter to the VLAN
C) Deploy storm control to block unknown unicast traffic
D) Use persistent MAC learning
Correct Answer:
Verified
Q37: What are two interarea OSPF LSA types?
Q44: Which mechanism is used to share routes
Q75: Which two statements describe BGP attributes? (Choose
Q94: Click the Exhibit button. Q95: Click the Exhibit button. Q96: Click the Exhibit button. Q97: Click the Exhibit button. Q100: Click the Exhibit button. Q101: Which two routers belong to the 172.16.0.0/22 Q104: Click the Exhibit button. Unlock this Answer For Free Now! View this answer and more for free by performing one of the following actions Scan the QR code to install the App and get 2 free unlocks Unlock quizzes for free by uploading documents![]()
![]()
![]()
![]()
![]()
![]()

