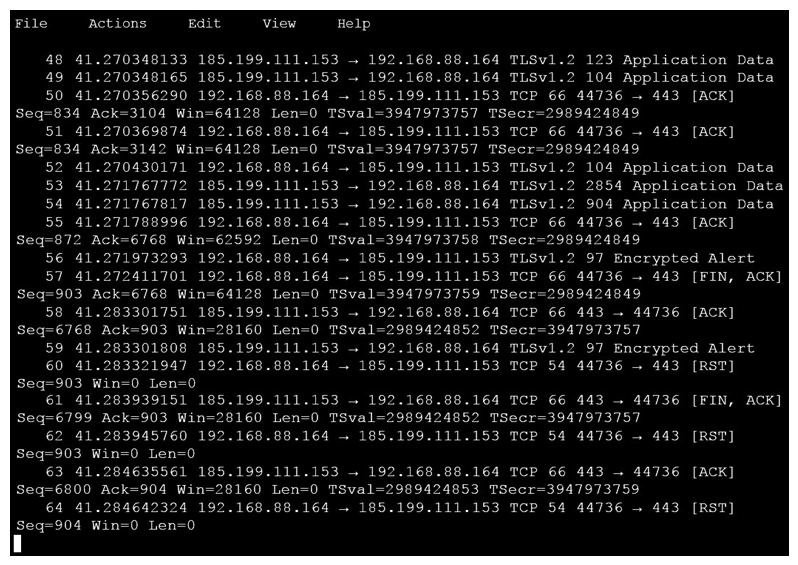
 An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
A) Base64 encoding
B) transport layer security encryption
C) SHA-256 hashing
D) ROT13 encryption
Correct Answer:
Verified
Q67: Which two components reduce the attack surface
Q68: In a SOC environment, what is a
Q69: Which open-sourced packet capture tool uses Linux
Q70: Which two elements are assets in the
Q71: Which utility blocks a host portscan?
A) HIDS
B)
Q73: Which category relates to improper use or
Q74: What should a security analyst consider when
Q75: What is personally identifiable information that must
Q76: What is rule-based detection when compared to
Q77: An investigator is examining a copy of
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents