Refer to the exhibit. 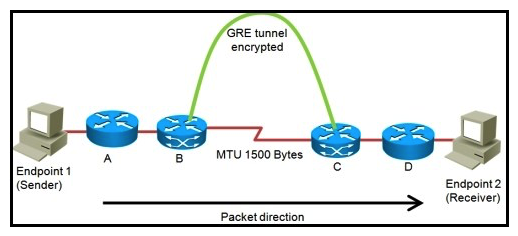 "Pass Any Exam. Any Time." - www.actualtests.com 53 Cisco 352-001 Exam You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
"Pass Any Exam. Any Time." - www.actualtests.com 53 Cisco 352-001 Exam You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
A) When router B fragments packets after the encryption, router C must reassemble these fragmented packets.
B) When router B fragments packets before the encryption, router C must reassemble these fragmented packets.
C) When router B fragments packets after the encryption, the endpoint 2 must reassemble these fragmented packets.
D) When router B fragments packets before the encryption, endpoint 2 must reassemble these fragmented packets.
E) When router A fragments packets, router C must reassemble these fragmented packets.
F) When router A fragments packets, endpoint 2 must reassemble these fragmented packets.
Correct Answer:
Verified
Q243: Which two techniques are used in a
Q244: You are designing the QoS features for
Q245: While reviewing an existing network design, you
Q246: Refer to the exhibit. "Pass Any Exam.
Q247: You are designing a network that includes
Q249: You are the lead network designer hired
Q250: Your design client has requested that you
Q251: Which two aspects are considered when designing
Q252: What is a key design aspect to
Q253: "Pass Any Exam. Any Time." - www.actualtests.com
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents