A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below: 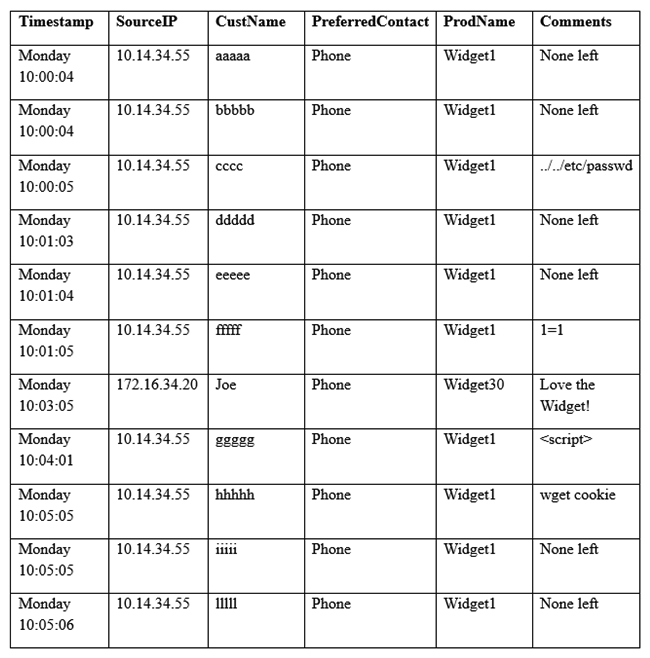 Which of the following is the MOST likely type of activity occurring?
Which of the following is the MOST likely type of activity occurring?
A) SQL injection
B) XSS scanning
C) Fuzzing
D) Brute forcing
Correct Answer:
Verified
Q52: A software development manager is running a
Q53: A company contracts a security engineer to
Q54: A new cluster of virtual servers has
Q55: While attending a meeting with the human
Q56: An organization enables BYOD but wants to
Q58: A network engineer is attempting to design-in
Q59: A security engineer is working with a
Q60: Legal counsel has notified the information security
Q61: An information security manager is concerned that
Q62: An organization is engaged in international business
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents