A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot. 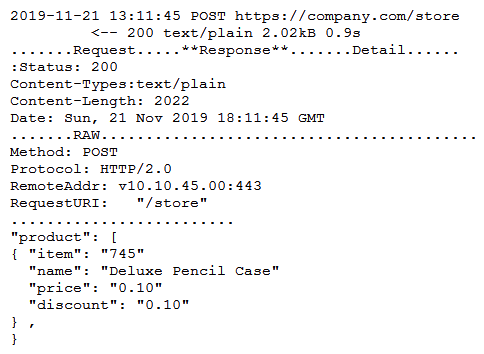 Which of the following tools was MOST likely used to exploit the application?
Which of the following tools was MOST likely used to exploit the application?
A) The engineer captured the data with a protocol analyzer, and then utilized Python to edit the data
B) The engineer queried the server and edited the data using an HTTP proxy interceptor
C) The engineer used a cross-site script sent via curl to edit the data
D) The engineer captured the HTTP headers, and then replaced the JSON data with a banner-grabbing tool
Correct Answer:
Verified
Q136: An organization is improving its web services
Q137: A technician is configuring security options on
Q138: The Chief Information Security Officer (CISO) suspects
Q139: A network printer needs Internet access to
Q140: A security engineer is assisting a developer
Q142: Joe, a penetration tester, is assessing the
Q143: A networking administrator was recently promoted to
Q144: A security administrator is advocating for enforcement
Q145: A network administrator is concerned about a
Q146: A government contractor was the victim of
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents