An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data: 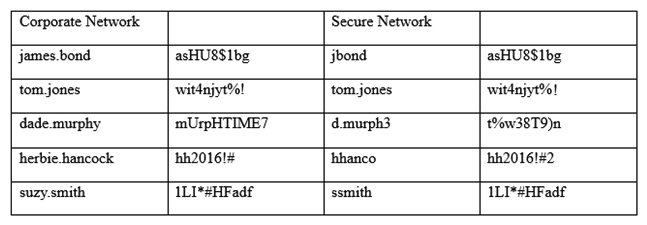 Which of the following tools was used to gather this information from the hashed values in the file?
Which of the following tools was used to gather this information from the hashed values in the file?
A) Vulnerability scanner
B) Fuzzer
C) MD5 generator
D) Password cracker
E) Protocol analyzer
Correct Answer:
Verified
Q273: Following a security assessment, the Chief Information
Q274: The code snippet below controls all electronic
Q275: A security engineer is designing a system
Q276: Ann, a member of the finance department
Q277: A security controls assessor intends to perform
Q279: The Chief Information Officer (CISO) is concerned
Q280: A forensic analyst suspects that a buffer
Q281: After several industry competitors suffered data loss
Q282: A security manager recently categorized an information
Q283: As part of incident response, a technician
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents