While investigating suspicious activity on a server, a security administrator runs the following report: 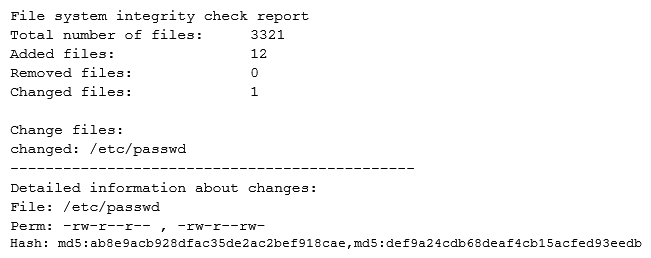 In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
A) An attacker compromised the server and may have used a collision hash in the MD5 algorithm to hide the changes to the /etc/shadow file
B) An attacker compromised the server and may have also compromised the file integrity database to hide the changes to the /etc/shadow file
C) An attacker compromised the server and may have installed a rootkit to always generate valid MD5 hashes to hide the changes to the /etc/shadow file
D) An attacker compromised the server and may have used MD5 collision hashes to generate valid passwords, allowing further access to administrator accounts on the server
E) An attacker compromised the server and may have used SELinux mandatory access controls to hide the changes to the /etc/shadow file
Correct Answer:
Verified
Q328: Following a recent and very large corporate
Q329: As part of an organization's compliance program,
Q330: A vendor develops a mobile application for
Q331: An organization's network security administrator has been
Q332: A security engineer is assessing the controls
Q334: A company recently implemented a new cloud
Q335: Developers are working on a new feature
Q336: An incident responder wants to capture volatile
Q337: A security architect has been assigned to
Q338: A project manager is working with a
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents