A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands: 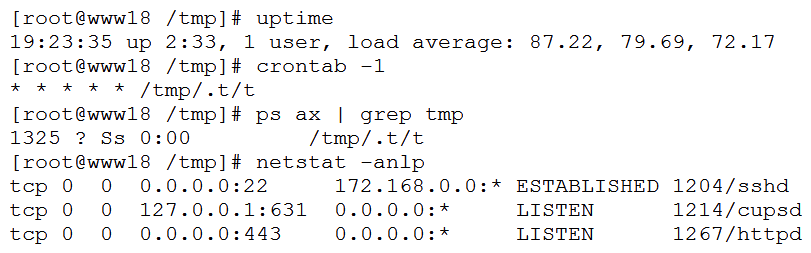 Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
A) Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system. Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system.
B) Examine the server logs for further indicators of compromise of a web application.
C) Run kill -9 1325 to bring the load average down so the server is usable again. kill -9 1325 to bring the load average down so the server is usable again.
D) Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server. Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server.
Correct Answer:
Verified
Q80: A security analyst discovers accounts in sensitive
Q81: A security analyst is reviewing packet captures
Q82: A user's computer has been running slowly
Q83: An analyst is working with a network
Q84: An analyst is performing penetration testing and
Q86: A cybersecurity analyst is contributing to a
Q87: A security analyst received an alert from
Q88: Data spillage occurred when an employee accidentally
Q89: A company was recently awarded several large
Q90: A security analyst for a large financial
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents