A penetration tester identifies the following findings during an external vulnerability scan: 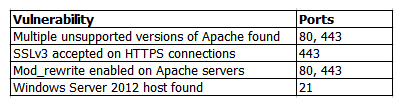 Which of the following attack strategies should be prioritized from the scan results above?
Which of the following attack strategies should be prioritized from the scan results above?
A) Obsolete software may contain exploitable components.
B) Weak password management practices may be employed.
C) Cryptographically weak protocols may be intercepted.
D) Web server configurations may reveal sensitive information.
Correct Answer:
Verified
Q5: Black box penetration testing strategy provides the
Q6: A client has scheduled a wireless penetration
Q7: Which of the following CPU registers does
Q8: A penetration tester is able to move
Q9: An energy company contracted a security firm
Q11: A penetration tester has compromised a Windows
Q12: Which of the following commands starts the
Q13: A malicious user wants to perform an
Q14: A penetration tester wants to target NETBIOS
Q15: A penetration tester executes the following commands:
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents