Click the exhibit button. 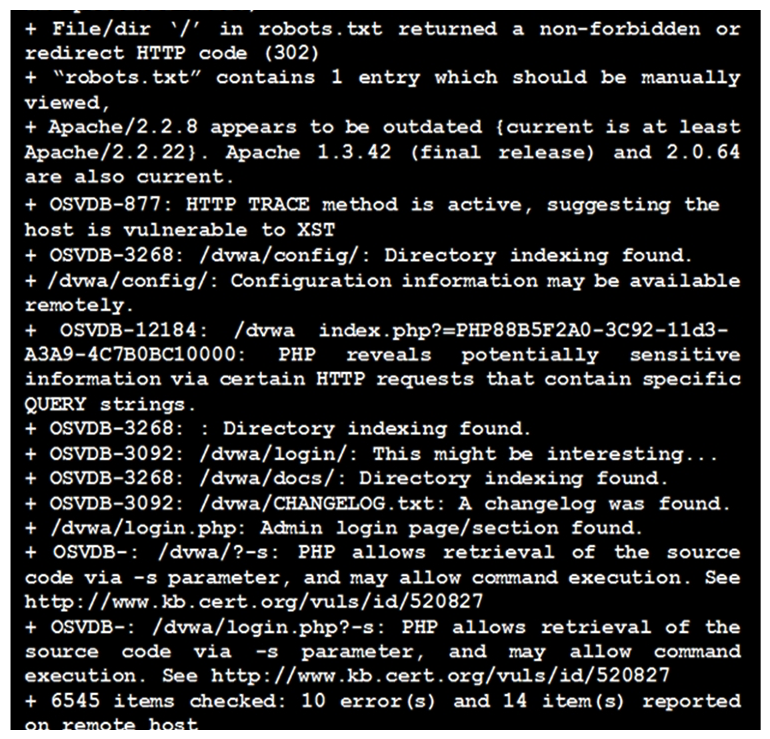 Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
A) Arbitrary code execution
B) Session hijacking
C) SQL injection
D) Login credential brute-forcing
E) Cross-site request forgery
Correct Answer:
Verified
Q37: During testing, a critical vulnerability is discovered
Q38: A security guard observes an individual entering
Q39: A penetration tester is scanning a network
Q40: A penetration tester has successfully deployed an
Q41: A penetration test was performed by an
Q43: In which of the following components is
Q44: A client asks a penetration tester to
Q45: A software development team recently migrated to
Q46: A penetration tester is checking a script
Q47: Which of the following vulnerabilities are MOST
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents