A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network. 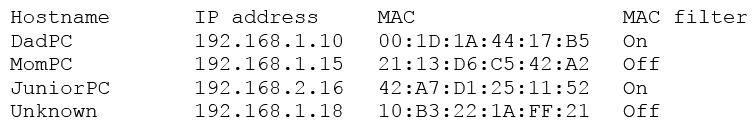 Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
A) Apply MAC filtering and see if the router drops any of the systems.
B) Physically check each of the authorized systems to determine if they are logged onto the network.
C) Deny the "unknown" host because the hostname is not known and MAC filtering is not applied to this host.
D) Conduct a ping sweep of each of the authorized systems and see if an echo response is received.
Correct Answer:
Verified
Q630: A security analyst receives the following output:
Q631: A security administrator is working with the
Q632: While testing a new application, a developer
Q633: When performing data acquisition on a workstation,
Q634: A user has attempted to access data
Q636: Which of the following BEST explains "likelihood
Q637: A systems administrator just issued the ssh-keygen
Q638: A technician wants to configure a wireless
Q639: Which of the following controls does a
Q640: A newly hired Chief Security Officer (CSO)
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents