A system administrator is reviewing the following information from a compromised server. 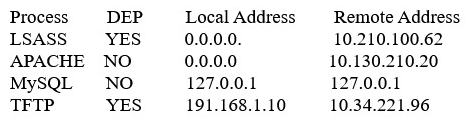 Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
A) Apache
B) LSASS
C) MySQL
D) TFTP
Correct Answer:
Verified
Q747: An application team is performing a load-balancing
Q748: An application developer is designing an application
Q749: Multiple organizations operating in the same vertical
Q750: A company was recently audited by a
Q751: A system's administrator has finished configuring firewall
Q753: An auditor is reviewing the following output
Q754: Before an infection was detected, several of
Q755: A company has a data system with
Q756: A Chief Information Officer (CIO) drafts an
Q757: Which of the following types of keys
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents