A security analyst reviews the following output: 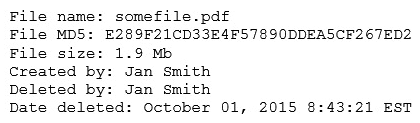 The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following: 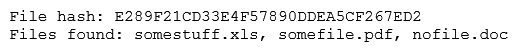 Which of the following is the MOST likely cause of the hash being found in other areas?
Which of the following is the MOST likely cause of the hash being found in other areas?
A) Jan Smith is an insider threat
B) There are MD5 hash collisions
C) The file is encrypted
D) Shadow copies are present
Correct Answer:
Verified
Q757: Which of the following types of keys
Q758: Which of the following must be intact
Q759: A company is currently using the following
Q760: A company hired a third-party firm to
Q761: A new mobile application is being developed
Q763: A security administrator receives an alert from
Q764: A help desk is troubleshooting user reports
Q765: An information security analyst needs to work
Q766: Technicians working with servers hosted at the
Q767: An administrator has configured a new Linux
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents