The following figure is an indication of the ___________ attack. 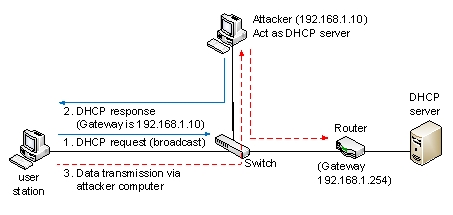
A) port scanning
B) packet sniffing
C) man-in-the-middle
D) social engineering
E) denial of service
Correct Answer:
Verified
Q12: Which CANNOT be spoofed for cyberattacks in
Q13: One key attribute that separates worms from
Q14: Zenmap (or nmap) is a popular program
Q15: Wireshark is a popular program for:
A) spamming
B)
Q16: A Free Video Player program comes with
Q18: What can be a method used for
Q19: Choose an INCORRECT statement on the virus
Q20: Choose an INCORRECT statement about the worm
Q21: Which may NOT be a popular form
Q22: The 'backdoor' is often created when a
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents