The following figure is an example of ___________ attack. 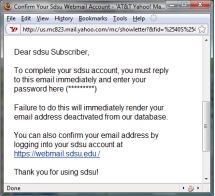
A) social engineering
B) denial of service
C) malware
D) fingerprinting
E) man-in-the-middle
Correct Answer:
Verified
Q3: Which CORRECTLY pairs a security layer and
Q4: Which is NOT a primary security requirement?
A)
Q5: _ is a process that validates "you
Q6: In realizing the defense-in-depth principle, the perimeter
Q7: The defense-in-depth principle may include security measures
Q8: The following elements/activities cut across all security
Q9: Maintaining a reliable backup system of corporate
Q10: Which of the following is NOT a
Q11: Maintaining data privacy achieves the _ aspect
Q13: Below email is an example of _:
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents