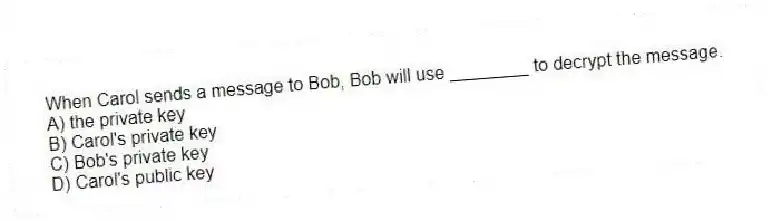
When Carol sends a message to Bob, Bob will use ________ to decrypt the message.
A) the private key
B) Carol's private key
C) Bob's private key
D) Carol's public key
Correct Answer:
Verified
Q42: When Joshua sends a message to Larry,
Q43: MS-CHAP provides mutual authentication.
Q44: Cryptanalysts have found weaknesses in _.
A) MD5
B)
Q45: What is the hash size of SHA-256?
A)
Q46: The most popular public key cipher is
Q48: Which encryption method does MS-CHAP use?
A) Symmetric
Q49: Public key encryption is _.
A) complex
B) slow
C)
Q50: _ are proofs of identity.
A) Certifications
B) Credentials
C)
Q51: When a hashing algorithm is applied, the
Q52: The hash size in MD-5 is 160
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents