Related Questions
Q46: The authenticator is the _.
A) workgroup switch
B)
Q47: When a new EAP authentication is added,
Q48: An EAP message begins with an _
Q49: _ is/are effective method(s) to preventing ARP
Q50: Eavesdropping usually is more of a concern
Q52: _ is called Port-Based Access Control.
A) 802.11i
B)
Q53: Most central authentication servers are governed by
Q54: When a new EAP authentication is added,
Q55: The main access threat to 802.11 wireless
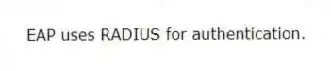
Q56: _ is used by _ for authentication.
A)
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents