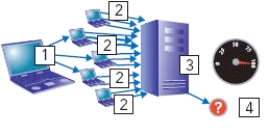
-Figure 6-2 shows a(n) ____ denial of service attack.
Correct Answer:
Verified
Q133: MATCHING
-a component of asymmetric encryption
A)spoofing
B)adware
C)steganography
D)spyware
E)port scan
F)port
G)hacker
H)necessity
I)authentication
J)secrecy
K)secret key
L)password
Q134: MATCHING
-verifying the identity of a person
A)spoofing
B)adware
C)steganography
D)spyware
E)port scan
F)port
G)hacker
H)necessity
I)authentication
J)secrecy
K)secret
Q135: A company can defend its Web server
Q136: A(n) _ examines the structure of the
Q137: In a(n) _ crime, a thief can
Q139: A(n) _ is a small, hidden graphic
Q140: A(n) _ vendor does not inform the
Q141: MATCHING
-occurs when data is disclosed to an
Q142: MATCHING
-hides encrypted messages within different types of
Q143: Name and describe the three basic types
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents